30 Aug Security Policy Framework
The security policy framework is the unifying structure that ties together an organization’s security documentation. Ensuring security is multi-layered process that extends throughout a business, agency or institution. Accordingly, an organization’s security policy framework encompasses the vision of its senior leadership, the laws and regulations that apply to its operations, and all of the specific guidance necessary to successfully achieve the security goals.
By giving structure to the variety of documents necessary for security, the framework helps to ensure that all of the important elements of a security process are in place, and that there is a vehicle for communicating these elements across the organization. There is a general hierarchy of documentation that organizations follow when establishing security policy frameworks. The different levels of the hierarchy address specific types communication needs and focus on a category of information and issues.
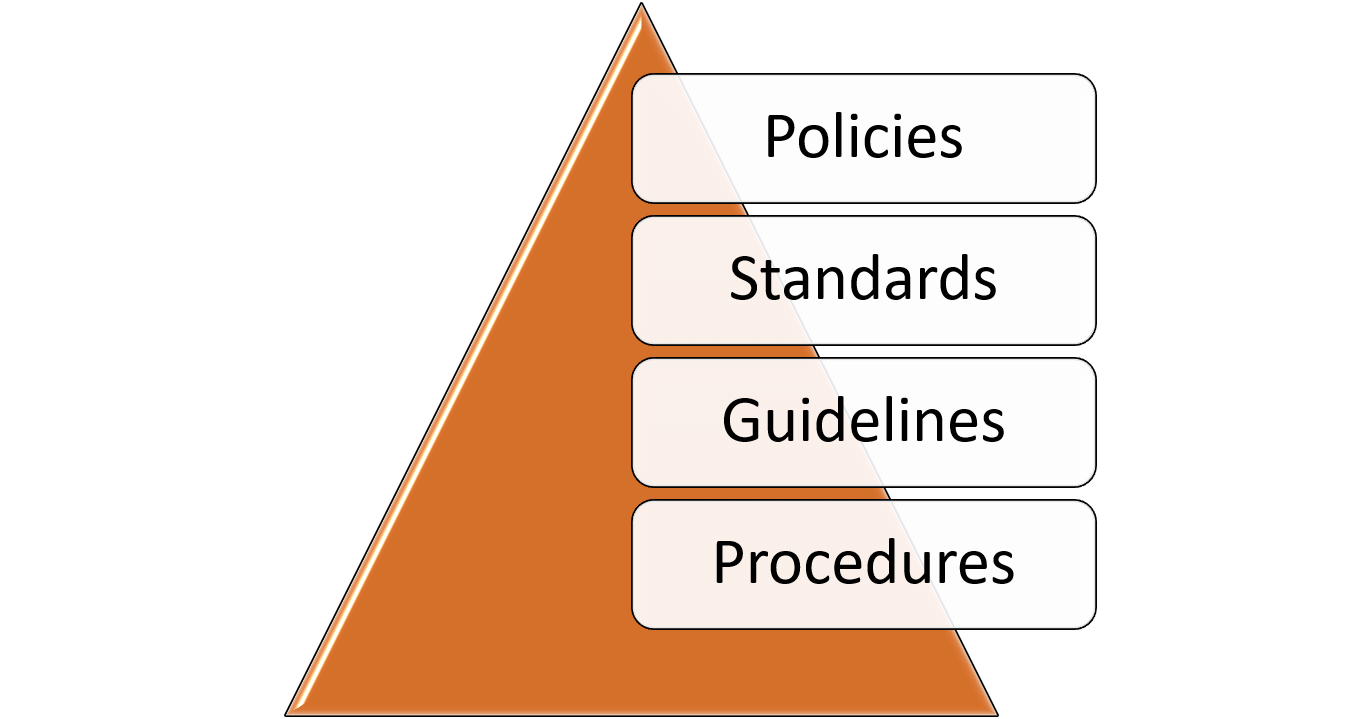
The security documentation hierarchy
At the top of the hierarchy are security policies, followed by standards, guidelines and procedures. If you are preparing for the CISSP, Security+, CySA+, or another security certification exam, you will need to have an understanding the security policy framework. You should be able to explain each level in the hierarchy, the types of information communicated at that level, and the importance of that type of communication to providing comprehensive security.
One important distinction to be made, is that compliance with policies, standards, and procedures is mandatory, guidelines are optional.
Security Policies
Security policies are high level documents that describe an organization’s security goals. They provide an overview of security needs, discussing the scope of the security that is needed and the resources required to provide that security.
There are three types of security policy:
- Organizational security policies
- Issue specific security policies
- System specific security policies
Every organization should have an organizational (or master) security policy. This policy is a strategic plan that presents the value of security to the organization and discusses the importance of security in all of the various activities within the organization. Features of an organizational security policy include defining roles, audit requirements, enforcement procedures, compliance requirements, and acceptable risk levels.
An issue-specific security policy focuses on a function or service within the organization that has distinct security requirements. Examples of issue-specific policies include an email policy, a media disposal policy, or a physical security policy.
A system-specific security policy is concerned with specific systems or types of system. It describes hardware and software approved for that system and how that system is to be protected.
In addition to the three focused types of security policy, there are three broad categories of policy: regulatory, advisory, and informative.
As its name implies, a regulatory policy discusses compliance issues for any regulatory frameworks that might apply to an organization, such as the Sarbanes-Oxley Act (SOX) of 2002 for finance firms, the Health Insurance Portability and Accountability Act (HIPAA) of 1996 for healthcare organizations, or any number of state and federal regulations that guide the way an organization manages security.
An advisory policy is used to communicate an organization’s internally driven standards for behaviors and activities. It presents the security ideals of the organization’s leadership and the consequences of security violations.
An informative policy is designed to enlighten employees about a specific security topic. Informative policies frequently provide background information in support of other security policies without any prescriptive actions or requirements.
Adherence to policies is mandatory.
Security Standards
Standards occupy the layer below policies in the hierarchy. They add specificity to the guidance, defining the instructions or methods that are necessary to achieve the objectives articulated in the security policies. Where policies are considered strategic documents, standards are tactical documents which provide a course of action. Compliance with standards is mandatory.
Baselines are related to standards and are sometimes considered an additional layer in the hierarchy. Baselines specify minimum levels of security that all systems must meet. They are often system specific and frequently refer to an industry or government standard. Common standards include the Trusted Computer System Evaluation Criteria (TCSEC), the Information Technology Security Evaluation and Criteria (ITSEC), and the NIST (National Institute of Standards and Technology) standards.
Security Guidelines
Guidelines are recommendations and practical guidance to help staff implement standards and baselines. Guidelines target all levels of staff including both security professionals and general users. They are intentionally flexible and are designed to be customized for new equipment and emerging situations.
Guidelines are considered suggested actions and compliance is therefore optional.
Security Procedures
Procedures make up the bottom layer of the documentation hierarchy. They are the most detailed and prescriptive of all the documentation. Procedures provide step-by-step instructions which guide staff in exactly how to correctly implement specific security controls. Procedures are very specific to the system or function they relate to and range from administrative duties to advanced hardware configuration. Examples of procedures include detailed instructions for configuring a router, installing antivirus software or sending an encrypted email.
Compliance with security procedures is mandatory.
Understanding the security policy framework is an important component of your preparation for a variety of security certification programs. If you’re interested in earning your next security certification, sign up for the free CertMike study groups for the CISSP, Security+, SSCP, or CySA+ exam.



No Comments